How to Use Cold Wallets for Maximum Security
- Understanding the importance of cold wallets in cryptocurrency security
- Setting up a cold wallet: step-by-step guide for beginners
- Best practices for storing and accessing your cold wallet securely
- Protecting your private keys: tips and tricks for cold wallet users
- Offline storage solutions: comparing different types of cold wallets
- Ensuring the safety of your funds: advanced security measures for cold wallets
Understanding the importance of cold wallets in cryptocurrency security
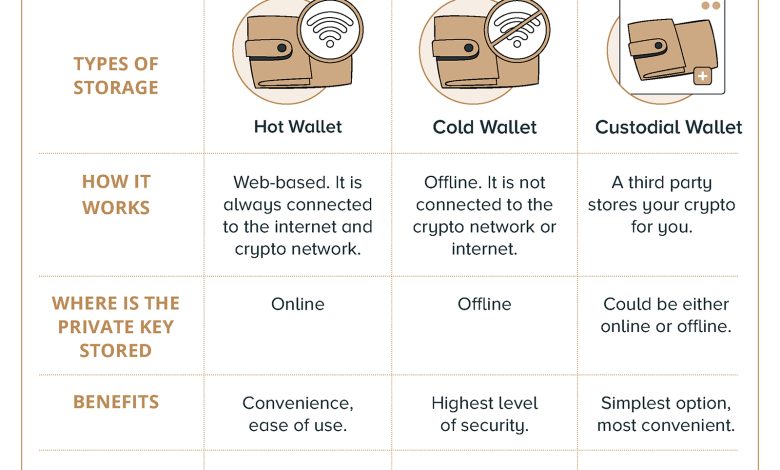
Understanding the significance of cold wallets in cryptocurrency security is crucial for anyone looking to safeguard their digital assets. Cold wallets, also known as hardware wallets, are physical devices that store private keys offline, making them less vulnerable to hacking and cyber attacks compared to hot wallets, which are connected to the internet.
By keeping private keys offline, cold wallets provide an extra layer of protection against unauthorized access and theft. This added security measure is especially important in the world of cryptocurrency, where transactions are irreversible and once funds are stolen, they are nearly impossible to recover.
Investing in a cold wallet is a proactive step towards securing your cryptocurrency holdings and ensuring peace of mind. While hot wallets are convenient for frequent trading and transactions, cold wallets are ideal for long-term storage of large amounts of cryptocurrency.
Overall, understanding the importance of cold wallets in cryptocurrency security is essential for anyone looking to protect their digital assets from potential threats and vulnerabilities in the ever-evolving landscape of the crypto market.
Setting up a cold wallet: step-by-step guide for beginners
Setting up a cold wallet is a crucial step in ensuring the security of your cryptocurrency holdings. Follow these step-by-step instructions to create a cold wallet for maximum protection:
- Choose a reputable hardware wallet: Select a hardware wallet from a trusted manufacturer to store your cryptocurrencies offline.
- Set up your hardware wallet: Follow the manufacturer’s instructions to initialize your hardware wallet and generate a new wallet address.
- Backup your seed phrase: Write down your seed phrase on a piece of paper and store it in a safe place. This seed phrase is essential for recovering your wallet in case it is lost or damaged.
- Transfer your cryptocurrencies: Send your cryptocurrencies from your exchange account to the wallet address generated by your hardware wallet.
- Verify your transactions: Check the transaction details on your hardware wallet to ensure that the funds have been successfully transferred.
- Secure your hardware wallet: Keep your hardware wallet in a secure location and protect it from theft, damage, or loss.
By following these steps, you can set up a cold wallet to safeguard your cryptocurrencies from online threats and hacking attempts. Remember to keep your seed phrase secure and never share it with anyone to maintain the security of your funds.
Best practices for storing and accessing your cold wallet securely
When it comes to storing and accessing your cold wallet securely, there are several best practices you should follow to ensure the safety of your crypto assets. Here are some tips to help you protect your investment:
- Keep your cold wallet offline at all times when not in use. This will prevent it from being hacked or compromised by cybercriminals.
- Store your recovery seed phrase in a secure and secret location. Do not share this information with anyone to avoid the risk of losing your crypto assets.
- Use a strong password to protect your cold wallet from unauthorized access. Make sure to change your password regularly for added security.
- Enable two-factor authentication (2FA) for an extra layer of protection when accessing your cold wallet. This will help prevent unauthorized transactions.
- Regularly update the software of your cold wallet to patch any security vulnerabilities and enhance its protection features.
By following these best practices, you can maximize the security of your cold wallet and keep your crypto assets safe from potential threats. Remember, protecting your investment is essential in the world of cryptocurrency.
Protecting your private keys: tips and tricks for cold wallet users
When it comes to using cold wallets for maximum security, protecting your private keys is crucial. Here are some tips and tricks for cold wallet users to ensure the safety of their keys:
- Store your private keys offline in a secure location, such as a safe or safety deposit box.
- Consider using a hardware wallet for added security, as they are designed to keep your keys safe from online threats.
- Avoid sharing your private keys with anyone, as this could compromise the security of your funds.
- Make sure to create a strong password for your cold wallet and never store it digitally.
- Regularly back up your private keys in multiple secure locations to prevent loss.
By following these tips and tricks, cold wallet users can ensure that their private keys are protected and their funds remain secure.
Offline storage solutions: comparing different types of cold wallets
When it comes to offline storage solutions, there are various types of cold wallets that can be used to maximize security for your cryptocurrency holdings. Let’s compare some of the different options available:
- Hardware Wallets: Hardware wallets are physical devices that store your private keys offline. They are considered one of the most secure options for cold storage, as they are not connected to the internet and are immune to hacking attempts.
- Paper Wallets: Paper wallets involve printing out your private keys and public addresses on a piece of paper. While they are secure from online attacks, they can be vulnerable to physical damage or loss.
- Brain Wallets: Brain wallets involve memorizing a passphrase that can be used to generate private keys. While they are convenient, they can also be risky if the passphrase is not strong enough.
- Steel Wallets: Steel wallets involve engraving your private keys on a piece of metal. This provides durability and protection against physical damage, but they can be cumbersome to use.
Each type of cold wallet has its own advantages and disadvantages, so it’s important to choose the one that best fits your needs and level of security. By using a cold wallet for offline storage, you can ensure that your cryptocurrency remains safe from online threats and hacking attempts.
Ensuring the safety of your funds: advanced security measures for cold wallets
When it comes to ensuring the safety of your funds, utilizing advanced security measures for cold wallets is crucial. Cold wallets are known for their offline storage capabilities, making them less susceptible to hacking and cyber attacks compared to hot wallets. Here are some key security measures to consider:
- Multi-signature functionality: Implementing multi-signature functionality adds an extra layer of security by requiring multiple private keys to authorize a transaction. This significantly reduces the risk of unauthorized access to your funds.
- Offline storage: Cold wallets store your private keys offline, making them inaccessible to hackers. By keeping your keys offline, you minimize the risk of them being compromised through online attacks.
- Hardware encryption: Many cold wallets come equipped with hardware encryption capabilities, ensuring that your private keys are securely stored and protected. This hardware-based security feature adds an extra level of protection to your funds.
- Backup and recovery options: It is essential to have backup and recovery options in place for your cold wallet. By creating secure backups of your private keys and having a recovery plan in case of loss or damage, you can safeguard your funds against unforeseen circumstances.
- Regular software updates: Keeping your cold wallet’s software up to date is crucial for maintaining optimal security. Software updates often include patches for known vulnerabilities, ensuring that your funds remain secure from potential threats.
By implementing these advanced security measures for your cold wallet, you can maximize the safety of your funds and protect them from potential security risks. It is essential to stay vigilant and proactive in safeguarding your cryptocurrency assets to ensure peace of mind and financial security.



